The hyped-up Mac malware story doesn’t show what it claims (yet)
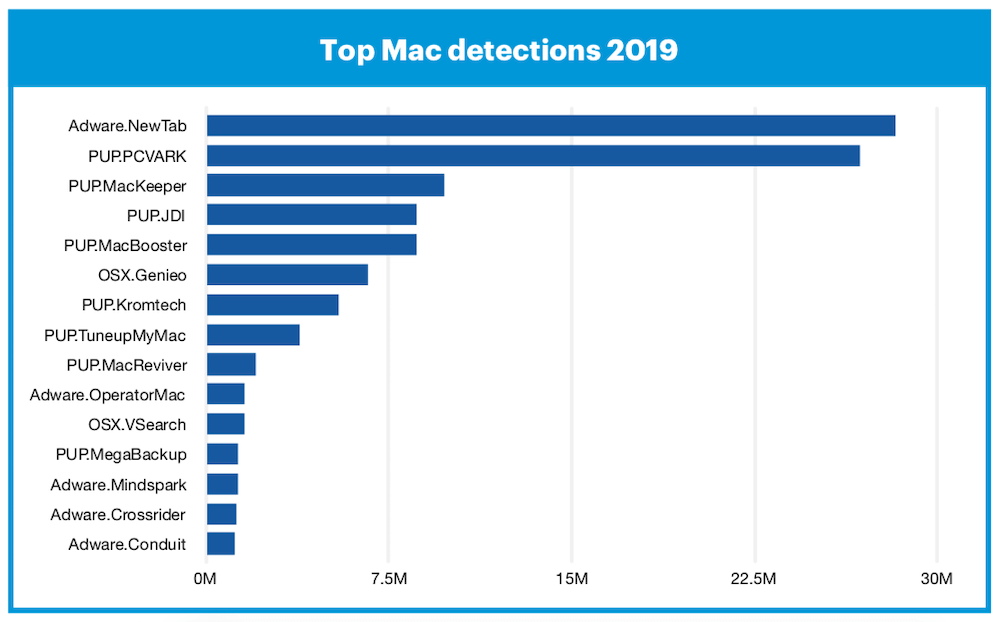
The report notes that most of these attempts come from MacKeeper, which no one should install really.
There’s been some misunderstanding following a recent Malwarebytes report, claiming to have identified twice as many attempts against Macs than Windows PCs in 2019 — the fact people are trying to climb the Apple security wall doesn’t mean they clambered over the top.
Another brick in the wall
That Macs are now more attractive to hackers, malware makers, adware creators and others doesn’t reflect the security weakness of the platform, but its growing value as an attack target.
Increasingly, the people who do the most business use Macs, and criminals behind the nastiest attempts are in the game of subverting platform security systems so they can make money.
In other words, the fact Apple’s platforms are becoming bigger targets than ever before means that Macs are being used more widely by the kind of people criminals want to target.
The fact that there’s increasing activity on the Mac reflects that when it comes to the seedy side of capitalism, criminals recognise a successful Mac attack may make money. There’s a profit motive
Numbers don’t tell the whole story
The thing is the numbers don’t tell the whole story. It is also interesting that so much of the focus on Mac security in response to the report actually skips what really should be more widely known claim:
That there has been a huge rise in the incidences of pre-installed malware and adware on Android devices.
In other words, you don’t even need to subvert Android security when they ship with built in adware.
I see that as a terrible indictment of security on that platform, and the blasé way in which its apologists shrug it off is sick to see.
What about Windows?
The report claims adware remains dominant, but ransomware attacks have grown more sophisticated and continue to target and subvert consumers and enterprises on that platform.
In other words, news that attacks against Macs have doubled is important, but what really matters is the number of Macs infected by malware, ransomware or other successful attacks.
And that number is small.
“Of all the threats seen this year, only one incident involved anything other than tricking the user into downloading and opening something they shouldn’t,” the report warns.
Not all threats are equal
It’s worth pointing out something else:
The majority of the threats against Macs aren’t truly threats at all.
“Most Mac threats, and certainly the most prevalent ones of 2019, are families of adware and potentially unwanted programs (PUPs),” the report claims.
That’s MacKeeper and MacBooster to most of us, spiced up with some horrid adware and software that spoofs you into downloading something less trivial.
That’s not to minimize the threat landscape, but it is true to say those threats that have captured the headlines around Mac security are more annoyances, than threatening.
But you shouldn’t be complacent.
Security is always a game in progress
There has always been a cat and mouse game between platform providers and cybercriminals.
The latter are far from stupid – they are tech-savvy, industry aware and determined folks usually motivated by money.
This means they usually seek out the least secure paths to penetrate target systems, and Apple’s current Mac security protections have not cracked down on adware and PUPs to the same degree that they have malware at this time, which is why they seek to exploit them.
When it comes to more dangerous malware, this is why just two varieties, OSX.Generic.Suspiciou and OSX.FakeFileOpener, had over 300,000 detections. (Which means they were identified by Malwarebytes before infecting anything).
So, what protection does Apple provide?
Apple’s security protections include:
Think about it and you’ll see that Apple already offers a multi-layered series of security protections for Macs.
- Mac App Store approvals: The need to approve apps before they get sold on the Mac App Store isn’t quite perfect, a very small number of bad actors may get through very rarely, but errors are quickly addressed. Mac users who only download software from here are very likely fine.
- App Notarization: Third party developers who want to sell their apps outside Apple’s Mac App Store can submit their software to Apple for notarization. Apple’s Notary Service will then automatically perform security checks on the software to ensure the installations are malware-free, signed correctly and that they use the appropriate runtime. More on this here.
- Gatekeeper: This kicks in when you try to launch an application. Unless the software passes some checks, it won’t run. Users can disable this protection if they wish, but that’s a more complex process designed to ensure users are aware of the risk they run when they switch such protection off. So, if you aren’t sure what you are doing, don’t do it.
- Software updates: Apple also has a highly effective software distribution system and its customers are inclined to update their systems soon after any patches ship. This means the company can quickly inoculate its platforms against any emerging major threat.
Apple will remove software it finds to be deceptive, to carry ads or otherwise degrade security or privacy.
In future, it seems we may see the company limit some of what you can do using traditional Unix Shell commands, as malware writers are beginning to explore the exploitation of these.
Put it all together and it seems pretty clear that Apple’s security teams are equipped to work fast in response to new threats.
Now they see that adware and unwanted applications are becoming a challenge to the platform, they will respond.
Ignorance is not power
People do think Macs “don’t get viruses”.
This is not true, but it’s easy to see why they think so — successful infections hardly ever happen.
Those attacks that do take place usually require attackers have physical access to the Mac (or a USB key subsequently connected to that Mac), though criminals continue to kick the platform around to see what they can break in order to enable remote exploits.
It is also worth observing that the Mac threatscape isn’t just about viruses or malware, but also includes spoof websites, phishing, personalized attacks on individuals, and attempts to trick people into sharing information they should not share, such as passcodes.
The real truth about Mac security (or the security of any platform that doesn’t happen to ship with malware pre-installed at the factory) is that the most insecure part of any Mac is not actually the Mac, but the user.
You are the weakest link.
What can you do?
Awareness keeps you safe. That and a little planning. This is why I recommend Mac users should:
- Avoid clicking links from people you don’t know.
- Do not install software from outside the App Store unless you know where it is from.
- Use strong passwords, and never use the same one twice.
- Use 2FA.
- Use a disposable email for services, websites and so forth.
- Never access confidential services (particularly banking) using public Wi-Fi.
- Install software updates as they ship.
- Enable all the privacy protections you can on your Mac.
- I also run a virus checker every now and then to ensure I don’t host any infected assets that don’t impact my Mac but which might harm someone else.
The best advice?
Don’t be complacent
That Apple’s platform security is attracting more attention than before is completely expected. Security analysts have been predicting it for a decade, ever since they noticed people were migrating to Mac and the Windows monoculture age was failing.
Don’t just assume everything is safe, don’t buy into the hype, but do make sure you control the risks you take.
Please follow me on Twitter, or join me in the AppleHolic’s bar & grill and Apple Discussions groups on MeWe.